Email Tracing:

In some cases, you may want to know the origin of some e-mails:
- When you are suspicious with a particular e-mail.
- When a friend asks you about an e-mail you never send. There are two possible explanations: (1) your computer has been hijacked by nasty viruses/worms and sent out e-mails without your knowing; (2) somebody else uses your e-mail address for the e-mails he/she sent. Whatever the case is, you want to know the truth.
- Someone contacts you for a job offer, and before you want to proceed any further, you may need to know more about this guy.
This short tutorial explains the basic of the e-mail system work and how to this knowledge to trace e-mails. Tracing an e-mail is not as hard as you might think. Let's begin to see how it works.
Route of an e-mail message
Mostly people send and receive e-mail messages with
E-Mail Client software. Microsoft Outlook, Outlook Express, Netscape Communicator, Eudora and Pegasus are examples of widely used e-mail clients.
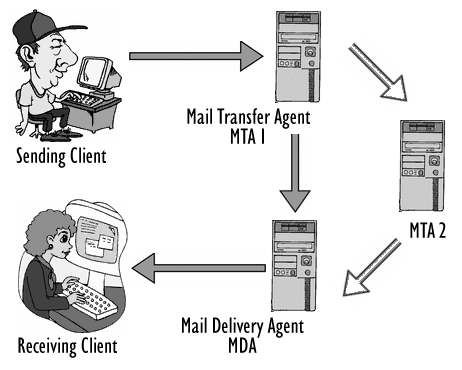
When you send your e-mail, you send it to a SMTP server called
Mail Transfer Agent (MTA). SMTP stands for
Simple Mail Transfer Protocol. Protocol is a standard for network communication. Your friend uses her e-mail client to access a server called
Mail Delivery Agent (MDA). MTA is responsible for transferring your e-mail to the recipient MDA. It may transfer it directly to the MDA, or indirectly via other MTAs. Your e-mail route could be one of the following routes:
- Sending Client - Sending MTA - Receiving MDA - Receiving Client.
- Sending Client - Sending MTA - (one or more other MTAs) - Receiving MDA - Receiving Client.
Each MTA and MDA is also called a
node in the route. The purpose of e-mail tracing / tracking is to find out the identity of each node along the route to the original sender. Each node along the route add a piece of information in the e-mail header section. We trace the e-mail by carefully studying this section.
E-mail headers
An e-mail message contains two main sections: header section and body section. Headers are used to convey control information of the e-mail; while body is used to convey the actual data (the e-mail content). It is like your paper mail or package. The header is the mail envelope and packing documents, while the body is the content inside the envelope or package.
Each node along the e-mail route add a piece of information, except the receiving mail client software. The most important piece of information for e-mail delivery is created by sending e-mail client software. It describes the recipient of the message. However, information created by sender is also the most unreliable. Some senders use fake identities or impersonate other individuals. The information created by your MDA should be considered reliable. We should treat information from other MTAs as quasi-reliable. As the rule of thumb, the closer a MTA to the receiving end, the more reliable it is.
How To Display E-mail Headers
Almost every email clients is different and because of that we have a slightly different steps to trace email header that is needed to track email IP address. Here are a couple most popular:
1.) To find, view and trace Email header for Gmail:
When you open email you will see next to the button "Reply" - down arrow. Click on arrow and choose "Show original". New window will be opened with full email header. Copy and paste full email header to start email tracking.
2.) To find, view and trace Email header for Yahoo Email:
If you right click on the email message you will see option "View Full Headers". Select it and new pop-up "Full Message Header" will appear. Copy and paste all email sources into our free email tracking tool to start tracing Email IP.
3.) To find, view and trace Email header Hotmail (Live) :
If you right click on the email message you will see option "View Message Source". Click with left mouse button and new window with the full email header sources will open. Copy and paste email header into our free email tracking tool for email header analysis.
4.) To find, view and trace email header in Outlook / Incredimail:
Select or open email message. Top left on your screen select "File" and then "Properties". Select then tab "Details" and eventually "Message source". Copy email header source and paste to be able to perform email tracking lookup and trace email IP location of sender.
Headers Created by Sending E-mail Client.
Sender e-mail client software may create some of these headers:
| Date: | Original sending date |
| From: | Author(s) of the message |
| Sender: | Actual submitter of the message |
| To: | Primary destination |
| Cc: | Secondary destination (Carbon Copy) |
| Bcc: | Blind Carbon Copy. Same with Cc, but e-mail addresses listed here are not forwarded to each recipient. |
| Reply-To: | Address to reply to. Default reply-to address is From, reply-to-author. However, you may specify a different address to reply-to. |
| Message-Id: | A unique identifier for each message. Message-Ids are provided by Sender e-mail client or Sender MTA. Often a message is a response to a previous message, Message-Id is then the identifier for the header References and In-Reply-To. |
| Organization: | Organization the sender affiliated with. |
| Subject: | Subject or summary of the message. |
| In-Reply-To: | Message-Ids of the parent (previous) messages. |
| References: | Message-Ids of other correspondences. |
| MIME-Version: | Version of the Internet message body format standard in use. MIME stands for Multipurpose Internet Mail Extensions. |
| Content-Type: | MIME type of the content is used in the message body. Some common values are:
text/plain, text/html, text/xml, text/enhanced, image/jpeg, image/gif, audio/basic, audio/au, video/mpeg, application/octet-stream, application/postscript, application/ms-word, application/ms-excel, application/rtf, multipart/mixed, multipart/alternative, multipart/parallel, multipart/related, message/rfc822, message/external-body. |
| Content-Transfer-Encoding: | MIME encoding used to represent data in a message for transfer using a mail transport protocol.
Common values include the following: - 7bit - Message contains 7-bit un-encoded US-ASCII data (Default).
- 8bit - Message contains 8-bit un-encoded data.
- binary - Message contains an un-encoded octet stream.
- quoted-printable - Message contents transformed to 7-bit US-ASCII using quoted-printable encoding algorithm.
- base64 - Message contents transformed to 7-bit US-ASCII using Base64 encoding algorithm.
|
| Disposition-Notification-To: | Indicates that the sender wants a disposition notification when this message is received by its recipients. |
| Keyword: | Rarely used. |
| Comments: | Rarely used. |
| Resent-*: | Headers with prefix Resent- are for forwarded messages |
| X-*: | All headers start with X- are additional features that have not yet made it into standard. |
| X-Mailer: | Information about the sender e-mail client software. |
| X-Priority: | Priority of the message. Values: 1 (Highest), 2 (High), 3 (Normal), 4 (Low), 5 (Lowest). 3 (Normal) is default if the field is omitted. |
Headers Created by Mail Transfer Agent (MTA).
A MTA may create one or some of these headers:
| Received: | This is the most important header created by an MTA. The most used format for this field is:
Received: from * by * with * id * for *; timestamp
from *: sending host
by *: receiving host
with *: link/mail protocol
id *: Message-Id generated or copied by the MTA
for *: destination in the field To
|
| Return-Path: | It shows the return path of the message, i.e., the address that bounces will be sent to. Final MTA should insert a return-path header containing the envelope sender address when the e-mail arrives at its final destination. Mostly MTAs insert the sender address in Return-Path. |
| Apparently-To: | Rarely inserted by MTA when there is no 'To:' recipient in the original message. Some mailing list hosts insert X-Apparently-To to the mails delivered to members of mailing-lists. |
| Mailing-List: | Mailing List ID or Name. Non-standard. Other mailing-list related headers may follow this header. |
| Delivered-To: | Used mostly for loop detection by many mailing-list hosts and autoresponders. |
Headers Created by Mail Delivery Agent (MDA).
Besides MTA headers above, some MDAs may have anti-spam or anti-virus features in their system. These systems may add some specific headers to an e-mail.
Let's trace e-mails
E-mail headers
An e-mail message contains two main sections: header section and body section. Headers are used to convey control information of the e-mail; while body is used to convey the actual data (the e-mail content). It is like your paper mail or package. The header is the mail envelope and packing documents, while the body is the content inside the envelope or package.
Each node along the e-mail route add a piece of information, except the receiving mail client software. The most important piece of information for e-mail delivery is created by sending e-mail client software. It describes the recipient of the message. However, information created by sender is also the most unreliable. Some senders use fake identities or impersonate other individuals. The information created by your MDA should be considered reliable. We should treat information from other MTAs as quasi-reliable. As the rule of thumb, the closer a MTA to the receiving end, the more reliable it is.
How To Display E-mail Headers
Let's trace e-mails
Below is a sample of an e-mail header.
X-Apparently-To: georgeburn@yahoo.ca via 206.190.38.42; Thu, 09 Dec 2004 01:08:32 -0800
X-YahooFilteredBulk: 172.182.209.16
X-Originating-IP: [172.182.209.16]
Return-Path: <vchia@tm.net.my>
Received: from 172.182.209.16 (EHLO tm.net.my) (172.182.209.16)
by mta128.mail.re2.yahoo.com with SMTP; Thu, 09 Dec 2004 01:08:32 -0800
From: vchia@tm.net.my
To: georgeburn@yahoo.ca
Subject: report
Date: Thu, 9 Dec 2004 10:08:28 +0100
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="----=_NextPart_000_0005_34D93898.B33F1947"
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MIMEOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
In the example,
georgeburn@yahoo.ca got an e-mail. From the domain name, he knew that items in blue color were generated by his mail server (yahoo.com), it should be consider reliable. The red headers however, are created by sender e-mail client.
From the red headers, the author claimed that he/she was
vchia@tm.net.my (see 'From' header), who used Microsoft Outlook Express 6 as the e-mail client. The e-mail address suggests it is an e-mail from Malaysia (TLD .my is for Malaysia).
However, the header created by the receiving mail server (mta128.mail.re2.yahoo.com) tells us that the origin IP address for this e-mail is 172.182.209.16. Let's us check the validity of sender's information with
Quis? Pro. Click links below for the full reports:
Query result of TM.NET.MY.
+---------------------------------------------+
¦ DOMAIN REPORT FOR: TM.NET.MY ¦
¦ by Quis? {WHOIS In Details} Jun 14, 2011 ¦
¦
http://gadget.stringcodes.com/quis/ ¦
+---------------------------------------------+
[Registrant MYNIC Handle : RGA000355]
Telekom Malaysia Berhad
709B, 6th Floor
Block E, Kelana Park View, No. 1 Jalan SS 6/2, Kelana Jaya
47301 Petaling Jaya
inetnum: 202.71.96.0 - 202.71.111.255
TM.NET.MY is owned by Telekom Malaysia. The IP Addresses allocated for this entity is [202.71.96.0 - 202.71.111.255]. IP Address 172.182.209.16 definitely does not belong to tm.net.my. The report for IP Address 172.182.209.16 reveals the real source. The e-mail originates from a US customer of America Online (AOL).

